Reliable, Scalable, and Cost-Effective Voice Connectivity for Your Business.
Criminals and unscrupulous robocallers often alter or spoof the calling number of their outbound telephone calls to deceive the called party. This deception can be as simple as changing the calling number so it appears that a neighbor is calling. This dishonesty raises the likelihood of the phoned party answering a robocall. Under other circumstances, the dishonesty might be more sinister, like a fraudster posing as an IRS agent pilfering a tax return. Spoofing is the act of changing the caller number of a phone call.
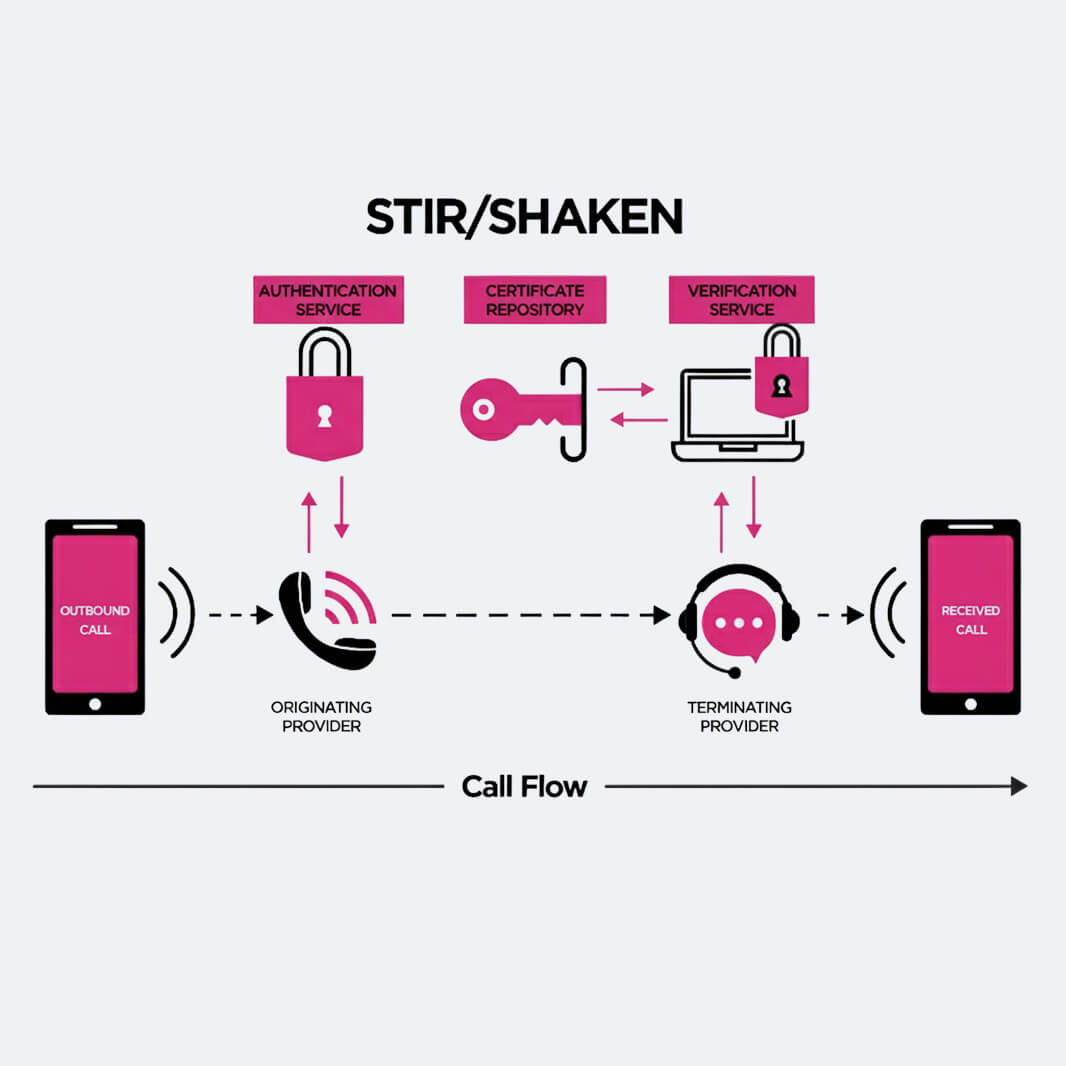

STIR/SHAken is a linked set of standards framework. Secure Telephone Identity Revisited (STIR) and Signature-based Handling of Asserted Information Using KENs (SHAKEN) standards have acronyms STIR/SHAKEN. Calls passing across linked phone networks can thus have their caller ID “signed” as legitimate by originating carriers and validated by other carriers before they ever reach customers. By digitally validates the handoff of phone calls flowing across the complicated web of networks, STIR/SHAKEN lets the consumer’s phone provider confirm that a call is in fact from the number shown on the Caller ID.
Based on conventional public key cryptography methods, STIR/SHAKEN guarantees the security of the calling number of a telephone call by using digital certificates. Simply said, every telephone service provider gets their digital certificate from a certificate authority that other telephone service providers trust. The called party can confirm that the calling number is accurate and unspoiled by certificate technology, therefore negating spoofing. Our whitepaper on Certificate Management for STIR/SHAKEN clarifies the specifics of how SHAKEN exploits public key infrastructure
The service provider has authenticated the calling party and they are authorized to use the calling number. An example of this case is a subscriber registered with the originating telephone service provider’s softswitch.
The service provider has authenticated the call origination, but cannot verify the call source is authorized to use the calling number. An example of this use case is a telephone number behind an enterprise PBX.
The service provider has authenticated from where it received the call, but cannot authenticate the call source. An example of this case would be a call received from an international gateway.
In essence, STIR is a technology, and SHAKEN is a policy. They work together to authenticate caller IDs and protect against multiple scams, including:

To fool victims into disclosing personal information, threat actors present as reputable institutions including banks, credit card firms, or government authorities. They can attempt to have victims provide one-time passwords and other information potentially compromising their identity. STIR/SHAKEN guards against phishing efforts by stopping hostile attempts at caller ID spoofing.

It’s short for “voice phishing.” Attackers trick targets into giving out sensitive information by impersonating a legitimate professional. They try to retrieve personal information or receive financial payments.
STIR/SHAKEN allows the phone company to verify if an incoming number is the same as the one on the caller ID. It prevents vishing attempts with digital validation of phone call handoff through complex networks.

Many threat actors impersonate a company’s tech support staff to convince victims of malware in their system. They encourage targets to update the software. While updating, the victim innocently gives away remote access to their computer.
Attackers leverage this to get the victim’s personal information. Sometimes, they may install malware or ransomware on the victim’s computer. STIR/SHAKEN prevents such incidents by verifying numbers with their caller IDs.

TOZCALL has done magic in market and connected all services on one platform. We provide VOIP, Fully Customized Dialling Solutions and many other platforms you think of.
Send Message
Solutions
Resources